Which of the Following Best Describes a Distributed Denial-of-service Attack
The primary technique consists of an attacker sending a DNS name lookup request to an open DNS server with the source address spoofed to be the. AWS Shield Advanced is an optional paid service.
What Is A Ddos Attack Identifying Denial Of Service Attacks
As used in this publication the term BIOS refers to conventional BIOS Extensible Firmware Interface EFI BIOS and Unified Extensible Firmware Interface UEFI BIOS.
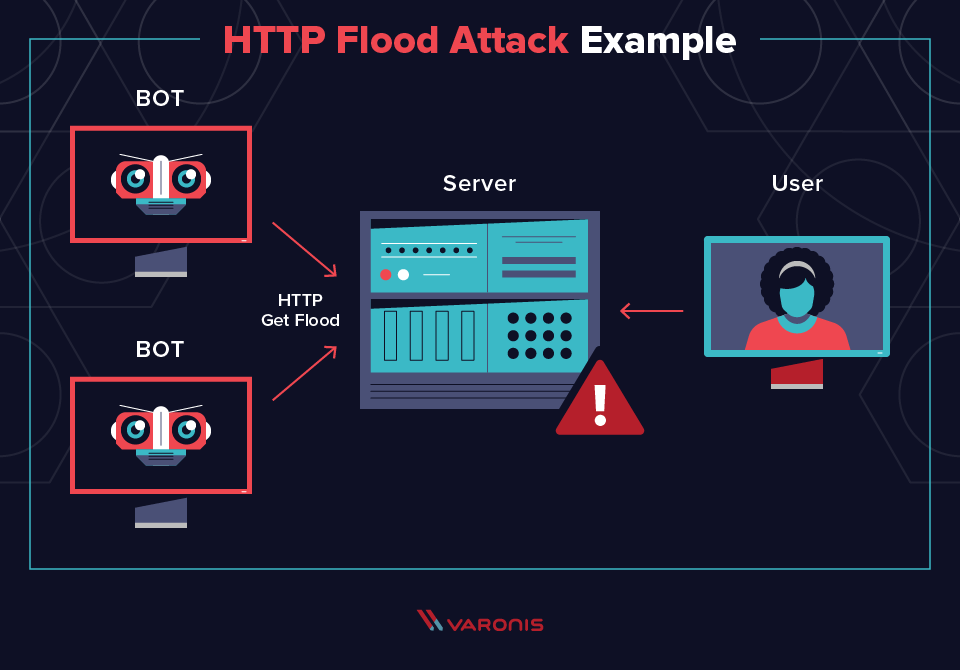
. Consider for example the following man-in-the-middle attack involving phony public keys. AWS Shield Standard is automatically enabled to all AWS customers at no additional cost. A Domain Name Server DNS Amplification attack is a popular form of Distributed Denial of Service DDoS in which attackers use publically accessible open DNS servers to flood a target system with DNS response traffic.
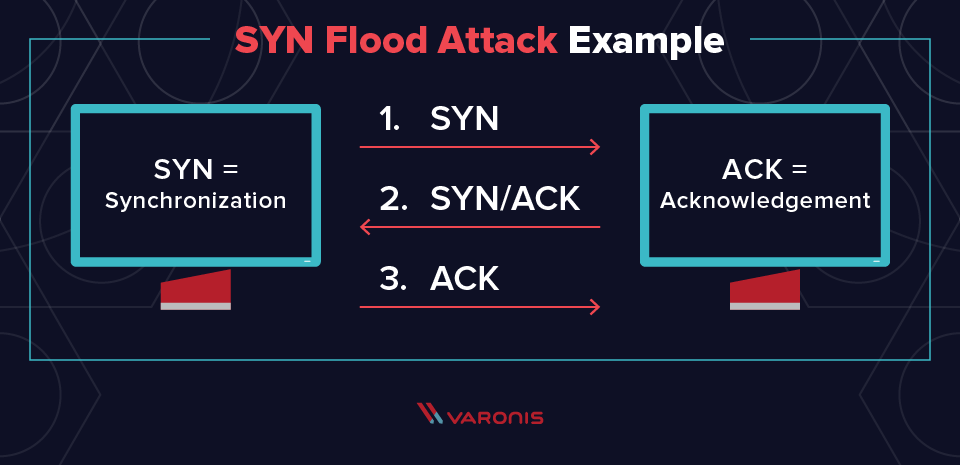
Figure 159 - A man-in-the-middle attack on asymmetric cryptography. Denial of Service DOS. These attacks can be politically ideologically or financially motivated or simply used to challenge and disrupt a public or private organization.
But wait a minute - How do we trust that third party and. AWS Shield Advanced provides additional protections against more sophisticated and larger attacks. One solution to the above problem involves digital certificates which are public keys that have been digitally signed by a trusted third party.
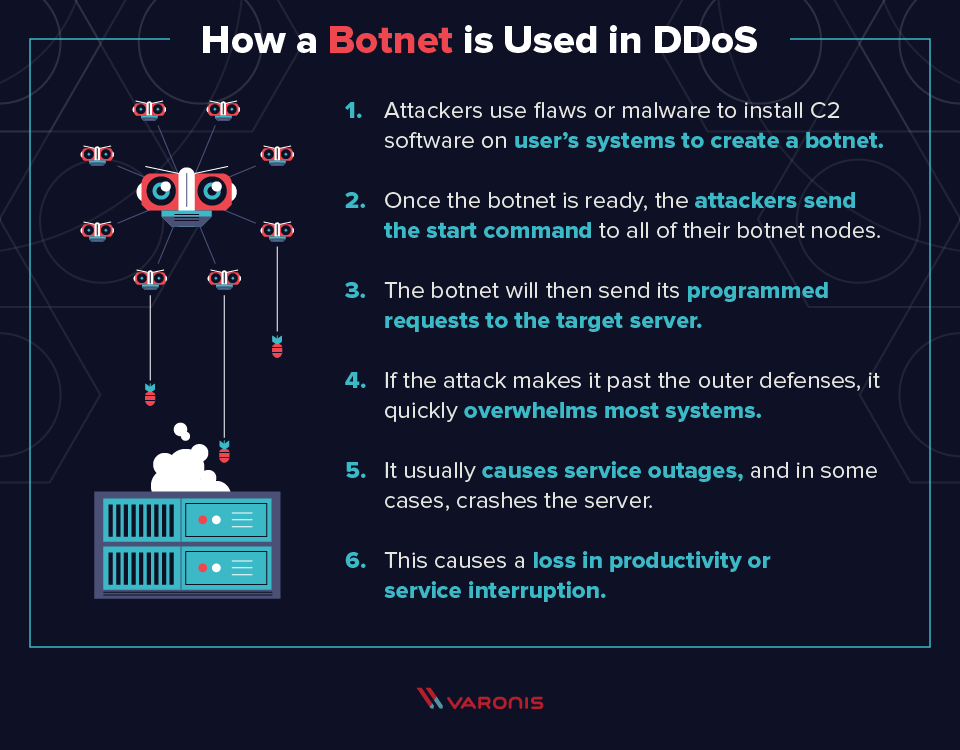
AWS Shield is a managed service that provides protection against Distributed Denial of Service DDoS attacks for applications running on AWS. Attack on an organization either a permanent denial of service if the BIOS is corrupted or a persistent malware presence if the BIOS is implanted with malware. The impact of a DDoS attack can range from temporary inconveniences to more noticeable effects including lost business opportunities and reputational damages from service disruption.
These criminal activities may also link to insider.
What Is A Ddos Attack Identifying Denial Of Service Attacks
No comments for "Which of the Following Best Describes a Distributed Denial-of-service Attack"
Post a Comment